This Item Ships For Free!
Trojan horse virus code new arrivals
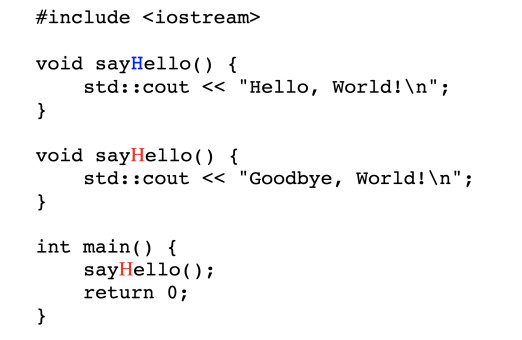
Trojan horse virus code new arrivals, Trojan Source attack method can hide bugs into open source code new arrivals
4.73
Trojan horse virus code new arrivals
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
Trojan Vs Virus Vs Worm What Is The Difference new arrivals, File Trojan Horse Virus Remover.png Wikimedia Commons new arrivals, Code Virus Over 102 804 Royalty Free Licensable Stock new arrivals, How to Tell if Your Computer Is Infected by a Trojan Horse new arrivals, Magnifying Glass Finds Trojan Horse in Computer Code Stock new arrivals, Premium Vector Trojan horse virus hacker hides a malware in a new arrivals, Python Based Trojan Horse Attack. How to perform a python based new arrivals, The story of a Chinese Banker Trojan Securelist new arrivals, Trojan Horse With Binary Code Isolated Stock Photo Download new arrivals, Charity Digital Topics What is trojan horse malware new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, How to Create a Trojan Virus in Kali Linux Live Linux USB new arrivals, Methods Cyber Attack Code Including Virus Stock Illustration new arrivals, What is a Trojan Virus Trojan Horse Malware Imperva new arrivals, The Ventir Trojan assemble your MacOS spy Securelist new arrivals, Anonymous hacker without face and trojan horse virus background new arrivals, How to effectively detect and mitigate Trojan Source attacks in new arrivals, Trojan Horse Program an overview ScienceDirect Topics new arrivals, RIP Copy and Paste from Stackoverflow Trojan Source Solution new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, Trojan Malware Unveiled All You Need to Know to Stay Safe new arrivals, Trojan Source attack method can hide bugs into open source code new arrivals, How to protect yourself against Trojan Source unicode attacks with new arrivals, Computer virus new arrivals, Trojan Malware What is a Trojan Virus IDStrong new arrivals, Placeholder Trojan Writing a Malware Software new arrivals, What is the Trojan Horse Virus SYSNETTECH Solutions new arrivals, Trojan horse conceptual image of Trojan malware computer virus new arrivals, Trojan Virus Quiz. Trojan Quiz by Examsegg Medium new arrivals, Computer Code Says Trojan Horse Stock Photo 641039281 Shutterstock new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, Trojan Horse 2 Lesson 1 How to create and bundle the metasploit new arrivals, Trojan Horse Virus Examples How to Defend Yourself new arrivals, Trojan Source attack method can hide bugs into open source code new arrivals, Python Trojan undetectable . I am going to be showing you how to new arrivals, Product Info: Trojan horse virus code new arrivals.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#7582346